US digital body to audit distributed computing security, Microsoft breach
WASHINGTON, Aug 11 (Reuters) - A U.S. digital security body will survey issues connecting with cloud-based character and verification framework that will incorporate an evaluation of a new Microsoft (MSFT.O) break that prompted the robbery of messages from U.S. government organizations, the Branch of Country Security (DHS) said on Friday.
The survey by the Digital Security Audit Board will take a gander at the noxious focus of distributed computing conditions, the DHS said in a statement. "Organizations of different sorts are progressively dependent on distributed computing to convey administrations to the American public, which makes it basic that we figure out the weaknesses of that innovation," DHS Secretary Alejandro Mayorkas said in the explanation.
The audit comes after U.S. Representative Ron Wyden in July asked the Government Exchange Commission, the Network Protection and Framework Security Organization and the Equity Division to "make a move" against Microsoft following the hack. Microsoft has been under expanding examination following disclosures that programmers supposedly working for Beijing's benefit got hold of one of its cryptographic keys and exploited a coding defect to acquire clearing admittance to the organization's cloud email stage.
The Digital Security Audit Board's survey will give suggestions to assist associations with safeguarding against malevolent admittance to cloud-based accounts, DHS said.
What is online protection?
Network safety is the security of web-associated frameworks, for example, equipment, programming and information from cyber threats. The training is utilized by people and undertakings to safeguard against unapproved admittance to server farms and other electronic systems. A solid network protection procedure can give a decent security pose against malignant assaults intended to get to, modify, erase, obliterate or blackmail an association's or alternately client's frameworks and delicate information. Online protection is likewise instrumental in forestalling assaults that plan to impair or disturb a framework's or alternately gadget's tasks.
For what reason is online protection significant?
With a rising number of clients, gadgets and projects in the advanced undertaking, joined with the expanded storm of information - - a lot of which is delicate or secret - - the significance of online protection keeps on developing. The developing volume and refinement of digital assailants and go-after strategies compound the issue even further. What are the components of online protection and how can it function?
The network protection field can be separated into a few distinct segments, the coordination of which inside the association is urgent to the progress of a network safety program. These segments incorporate the following
Application security
Data or information security
Network security
Fiasco recuperation/business congruity arranging
Functional security
Cloud Security
Basic framework security
Actual security
End-client instruction
Keeping up with online protection in a continually developing danger scene is quite difficult for all associations. Conventional responsive methodologies, in which assets were set toward safeguarding frameworks against the greatest known dangers, while less popular dangers were undefended, is presently not an adequate strategy. To stay aware of changing security gambles, a more proactive and versatile methodology is essential. A few key online protection warning associations offer direction. For instance, the Public Organization of Guidelines and Innovation (NIST) suggests embracing persistent observing and continuous evaluations as a component of a gamble appraisal structure to safeguard against known and obscure dangers.
What are the advantages of online protection?
The advantages of carrying out and keeping up with online protection rehearse include:
Business security against cyberattacks and information breaks.
Security for information and organizations.
Avoidance of unapproved client access.
Further developed recuperation time after a break.
Security for end clients and endpoint gadgets.
Administrative consistence.
Business congruity.
Further developed trust in the organization's standing and trust for designers, accomplices, clients, partners and employees.
What are the various sorts of network safety dangers?
Staying aware of new innovations, security patterns and danger insight is a difficult undertaking. It is vital to shield data and different resources from cyber threats, which take many structures. Sorts of cyber threats include:
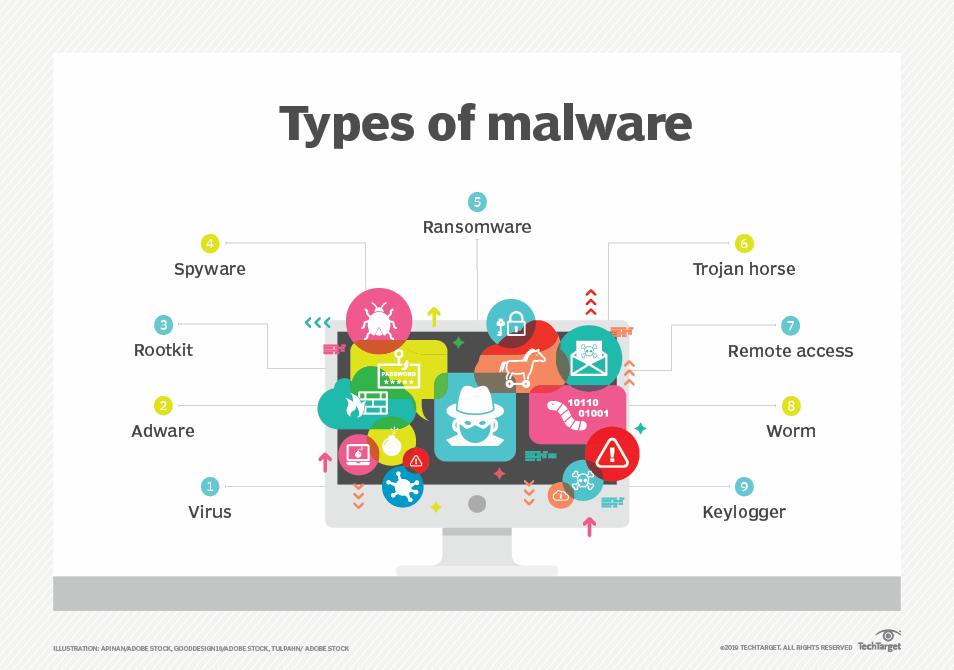
Malware is a type of malevolent programming wherein any record or program can be utilized to hurt a PC client. Various sorts of malware incorporate worms, infections, Trojans and spyware.
Ransomware is one more sort of malware that includes an assailant locking the casualty's PC framework documents - - regularly through encryption - - and requesting an installment to unscramble and open them.
Social designing is an assault that depends on human connection. It fools clients into breaking security methods to acquire delicate data that is ordinarily safeguarded.
Phishing is a type of social design where deceitful emails
or instant messages that look like those from trustworthy or realized sources are sent. Frequently irregular assaults, the plan of these messages is to take delicate information, for example, Visa or login data.
Stick phishing is a sort of phishing that has an expected objective client, association or business.
Insider dangers are security breaks or misfortunes brought about by people - - for instance, workers, workers for hire or clients. Insider dangers can be pernicious or careless in nature.
Disseminated refusal of administration (DDoS) assaults are those wherein numerous frameworks upset the traffic of a designated framework, like a server, site or other organization asset. By flooding the objective with messages, association solicitations or parcels, the aggressors can slow the framework or crash it, keeping real traffic from utilizing it.
High-level tenacious dangers (APTs) are drawn-out designated assaults in which an aggressor penetrates an organization and stays undetected for significant stretches of time with the expected to take information.
Man-in-the-center (MitM) assaults are snooping assaults that include an aggressor catching and transferring messages between two gatherings who accept they are speaking with one another.
Other normal assaults incorporate botnets, drive-by-download assaults, exploit packs, malvertising, vishing, qualification stuffing assaults, cross-web page prearranging (XSS) assaults, SQL infusion assaults, business email split the difference (BEC) and zero-day takes advantage of.


No comments:
Post a Comment